Whenever businesses or brands want to acquire a memorable web presence, they often purchase a short, easy-to-remember domain. While there are millions of domains with renewal costs of less than $20, others have been bought for a much higher price. This article will discuss some of the most expensive premium domain sales of all time.
In 2019, Block.one acquired Voice.com from MicroStrategy for $30 million, which set the record as the most expensive publicly-disclosed domain sale of all time.
Block.one put Voice.com to work hosting a blockchain-based social media platform, described as a decentralized version of Facebook or Medium. …
Today we officially launched our Premium DNS service that is designed to elevate the performance, accessibility, and security of your customers' websites. Our cutting-edge solutions utilize Anycast routing methodology with over 40 locations worldwide, and network addressing, where a single destination IP address is shared by multiple servers (PoPorNodes).
With our Premium DNS service, you can ensure that websites remain online even if a DNS server or zone experiences downtime. Our service enhances TTFB (time to first byte) by connecting visitors to the nearest name server location on our network, resulting in lightning-fast response times. Additionally, our solutions …
We are excited to announce our latest feature - Domain Bundling! You can now easily offer free bundled domains to your customers, providing added value and a unique offering.
For every existing domain in your portfolio, as well as any newly registered domains or transfers, you can easily register the equivalent in a promotional extension for free. This means you can offer your customers multiple domains at no extra cost for the first year, with no limit on the number of bundles.
Some of the benefits of domain bundling:
- Increase sales: Offer popular domain extensions as part of a …
Recently we added the ScamAdviser feed to our DNS Abuse Monitoring system. Based on the input and experience from our customers, I thought it would be helpful to cover a few items.
ScamAdviser is a reputation-based feed that differs from the Google Safety Browsing feed. If Google marks a domain name as malicious, it is no longer accessible as many browsers will now warn internet users not to visit the website.
ScamAdviser will inform you if the reputation of the domain name is poor. Of course, a lousy score depends on many factors, and ScamAdviser uses plenty. But a poor …
We have added an option to automatically lock domains created or transferred in with the setting "Auto-add ClientTransferProhibited".
You can enable this in your account details.
Next to that, you can now choose to "hide optional terms" in the contact validation emails sent to your customers. By default all available registry terms are presented. By enabling hide optional terms, only the specific terms for the requested TLD will be shown in the email sent after the create/transfer.
You can enable this in your brand details.
Last month, Realtime Register partnered with the Global Cyber Alliance (GCA) to expand the Realtime Register Insights Domain Abuse Platform capabilities.

At Realtime Register, we have been collecting abuse/intelligence feeds like Pokémon this year. By adding the GCA Domain Trust Feed we are now up to 72 feeds. The information gathered we make available to our resellers, providing them with deep insight into how criminals are using their services.
However, the Domain Trust Feed is not just a feed; it is much more.
Let’s get technical
The GCA uses the Quad9 feed. Quad9 protects users from accessing known malicious websites, …
In this article/faq, I will explain the security threat dashboarding/monitoring.
What is it?
In the first beta phase, we will make the threat intelligence we download from Pulsedive available to our customers in the domain manager.
If you are a customer of Realtime Register you can join the beta program.
Please contact our support team for information.
As a customer, you will be able to see the active security threats.
Security threats could be phishing domain names or malware domain names.
The Abuse Dashboarding provides you with information that usually does not get reported to Registrars.
As a result, you …
We are currently working on a project to provide abuse monitoring information to our customers.
Giving our customers just the raw data is not helpful, so our goal is to contextualize the data.
We still have long ways to go, but the basics are there.
So what do I see right now on our platform?
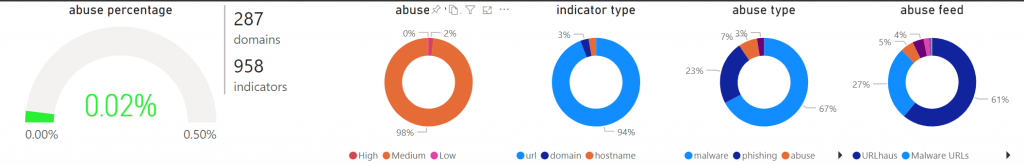
- Malware (67%)
- Phishing (23%)
- The rest falls into somewhat general buckets like BEC fraud, DGA, botnets, dark lists, crypto mining, etc. Very low incidental percentages.
The above-mentioned data is from two years of monitoring.
On the left is displayed the overall abuse percentage since …
RiskReact is a service of Realtime Register B.V. with a focus on security threats, cyber intelligence & OSINT.

Last year a registrar employee was the victim of social engineering resulting in an unauthorized transfer of a domain name.
A few months ago, a registrar employee was the victim of a spear-phishing attack, resulting in a DNS hijack.
A possible solution to counter such issues and other risks is a Domain Name Registry Lock.
Domain name registry locks are available for many TLDs. They all cover the same basic level of protection.
- Domain name update lock, preventing unauthorized or accidental updates …
In addition to the recent introduction of adding API keys, now we are adding Multi-Factor Authentication support. Multifactor authentication (MFA) is a security system that requires more than one method of authentication from independent categories of credentials to verify the user’s identity for a login or other transaction.

Multifactor authentication combines two or more independent credentials: what the user knows (password), what the user has (security token) and what the user is (biometric verification).
We will support the following methods for MFA:
- Webauthn (FIDO2) supporting Touch or Pin and Touch sensor like Yubikey with secure elements, Software authenticators and also …






